
The L-ADS is a soft real-time anomaly-based network intrusion detection system. It monitors the network traffic in segments of an OT infrastructure and detects anomalous behaviour in such communications. It offers a comprehensive network traffic monitoring from OSI layer 2 protocols to application layer OT protocols for ICS/SCADA substations.
The L-ADS features a high-level automation in both deployment and operation with minimal security expertise required. It automatically learns the normal behaviour of the different ICS/SCADA components, such as PLCs, RTUs, IEDs, HMI and SCADA servers, and monitors any deviation from the benign traffic model. The tool is driven by a custom bi-directional flow generator and two deep learning algorithms: one for the detection of anomalies and another one for recognition of potential attacks causing the anomalies.
Detection capabilities

The L-ADS inspects and analyses metadata of network packets, and for the most popular OT protocols, such as Modbus-TCP and DNP3, and in the power grid sector IEC 60870-5-104 and IEC 61850 GOOSE & SV, it provides a deep packet inspection. L-ADS derives a large number of behavioural characteristics from ICS/SCADA components’ communications, such as function codes utilisation, which empower the detection of anomalies and attacks. The anomalies represent any deviation from legitimate traffic. L-ADS provides explainability of why the anomalies are detected, with useful information on critical behavioral characteristics, their value difference and direction of intrusion.
L-ADS also adopts a new type of characteristics called conformity features that, in addition to the behavioral ones, indicate how much network traffic conforms (or does not) to the different legitimate dimensions indexed during training. These features reinforce L-ADS’s visibility on intrusions on border areas (between legit and anomalous) where advanced or stealthy attacks mostly evade detection. The L-ADS conformity monitoring ranges from monitoring whitelist IP (v4/v6) and MAC addresses to finer-grained monitoring of traffic conformity between legitimate entities in ICS/SCADA environments per protocol, per protocol and day of week, and even per hour a day. All conformity info is automatically indexed and configured during training.
The L-ADS offers custom deep leaning models and extended OT protocol monitoring for the most popular OT protocols as indicated above. It alerts on anomalies even when new, “zero-day” attacks take place. Whether an attacker performs a network reconnaissance or a lateral movement, the L-ADS will detect and alert such traffic.
It has been validated in several pilot OT environments (e.g., a substation of distribution power, and PV plant) under OT specific attacks, but also on several intrusion detection datasets1. A summary of LADS’s detection capability is listed below.
1. Promising high detection rate results achieved for all attacks in datasets IEC104,DNP3,Modbus,IEC61850.
| Generic attacks (IT protocols) | Man in the Middle (MitM) | |
|---|---|---|
| Packet Injection (forging/spoofing) | ||
| Unauthorised Host Access | ||
| Reconnaissance | Network Scanning, Port Scanning | |
| Denial of Service (DoS/DDoS) | TCP SYN Flood, ICMP Ping Flood, Blackholing | |
| OT protocol specific attacks ( ModbusTCP, DNP3, IEC104, IEC61850 GOOSE & SV) | Unauthorised Activity | Unauthorised Function Code use or misuse |
| Packet Injection | Injection of forged/spoofed OT protocol packets into legitimate communications | |
| Packet Replay | Replay of OT protocol packets from past sessions | |
| Reconnaissance | Enumerate / Info attack, Function Code Scanning | |
| DoS | Protocol/Function Code Level DoS such as selective Blackholing, Packet drop, (low rate) excess num. of Headers/Function Code payloads. | |
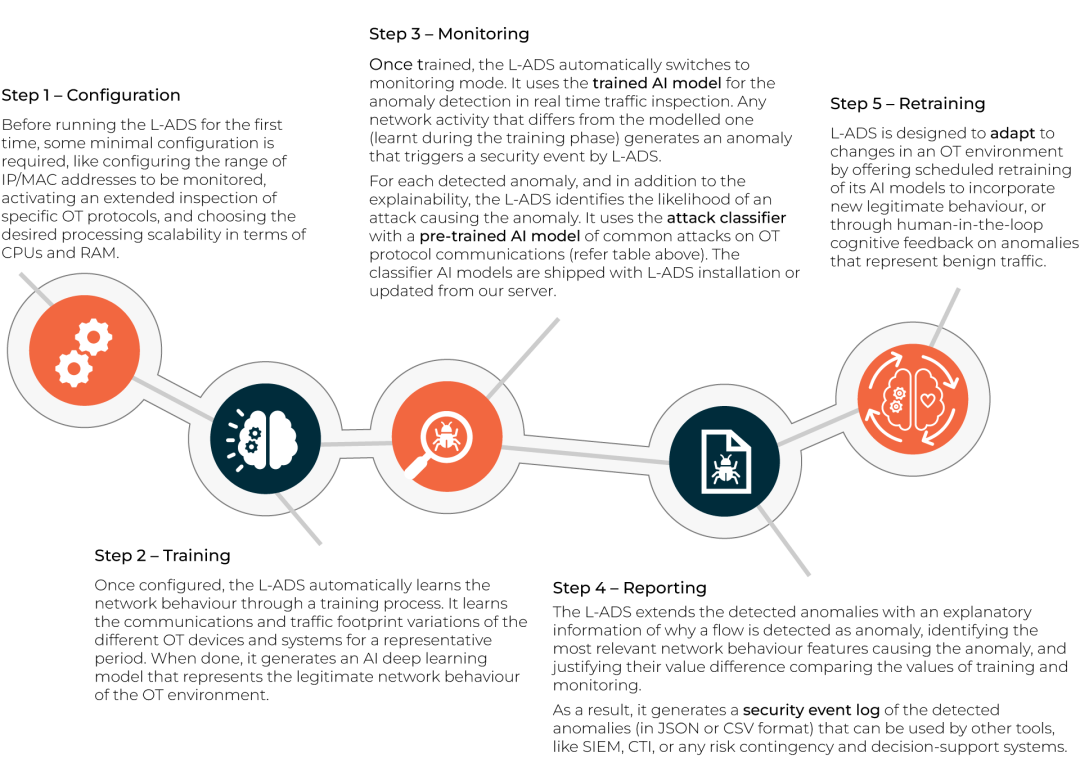
Setup and operation
In contrast with classic rule-based intrusion detection tools, the L-ADS does not require creation of customized rules, load specific rulesets or complex configurations for getting it started. Its setup process is much simpler and automatic than most classic IDSs.
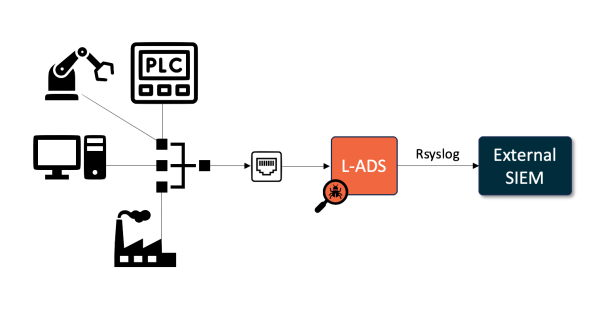
Deployment
The L-ADS is provided as a Docker container with a Compose file to ease its deployment and configuration. The L-ADS can be scaled to more complex infrastructures with segmented networks by deploying multiple instances at critical (e.g., gateway) points such as those of field or telecontrol LANs. The following diagram shows the typical deployment view of the L-ADS in an OT environment, but other deployments are well available across Edge-to-Cloud continuum.
Performance & requirements

The L-ADS performance depends on the performance of the hosted server and the available resources. However, the following resources are recommended for running the L-ADS stably:
| Requirements | Min | Recommended |
|---|---|---|
| RAM | 4 GB | 6 GB |
| vCPUs | 4 | 6 |
| HDD | 30 GB+ | 60 GB+ |

Using the recommended resources, the L-ADS is able to process and analyse up to 5500 data flows per second in real-time.

Additionally, the L-ADS only requires to be deployed in a system with Docker installed and VT-x enabled, within a dedicated network interface where real-time network traffic is mirrored to.